Manufacturing Process Simulation
Reverse engineering is the process of deconstructing a man-made object to understand its design, architecture, or to extract knowledge from the object. It's like taking a watch apart to see how all the gears and springs work together. This practice is vital in numerous industries, from software development to product manufacturing, and even in fields like cybersecurity and forensics. Achieve flawless replication of any component. Our in-house capabilities include precision 3D scanning, CNC machining, and advanced 3D printing to ensure every detail is captured with maximum precision.


Why Reverse Engineer?
The motivations behind reverse engineering are diverse:
Interoperability: To make different systems or components work together, especially when documentation is scarce or unavailable.
Maintenance: To repair, update, or improve existing systems, particularly legacy hardware or software.
Security Analysis: To identify vulnerabilities in software or hardware, crucial for protecting against cyber threats.
Competitive Analysis: To understand how a competitor's product works, allowing for the development of improved or alternative solutions.
Forensic Analysis: To investigate incidents, recover data, or understand the functionality of malicious software.
Learning and Education: To gain a deeper understanding of how complex systems are designed and implemented.
Key Benefits of Our Reverse Engineer Services

Reduce Costs: Identify and eliminate inefficiencies, optimize resource utilization, and minimize waste before costly physical implementation.
Increase Throughput: Pinpoint and alleviate bottlenecks, optimize flow, and maximize production capacity.
Mitigate Risk: Test new processes, layouts, or equipment virtually, avoiding expensive mistakes
Improve Decision Making: Gain data-driven insights to make informed choices about investments, scheduling, and operational changes.
Enhanced Flexibility: Quickly adapt to demands by simulating different scenarios and understanding their impact.
Initial Assessment and Planning
1. Initial Assessment and Planning


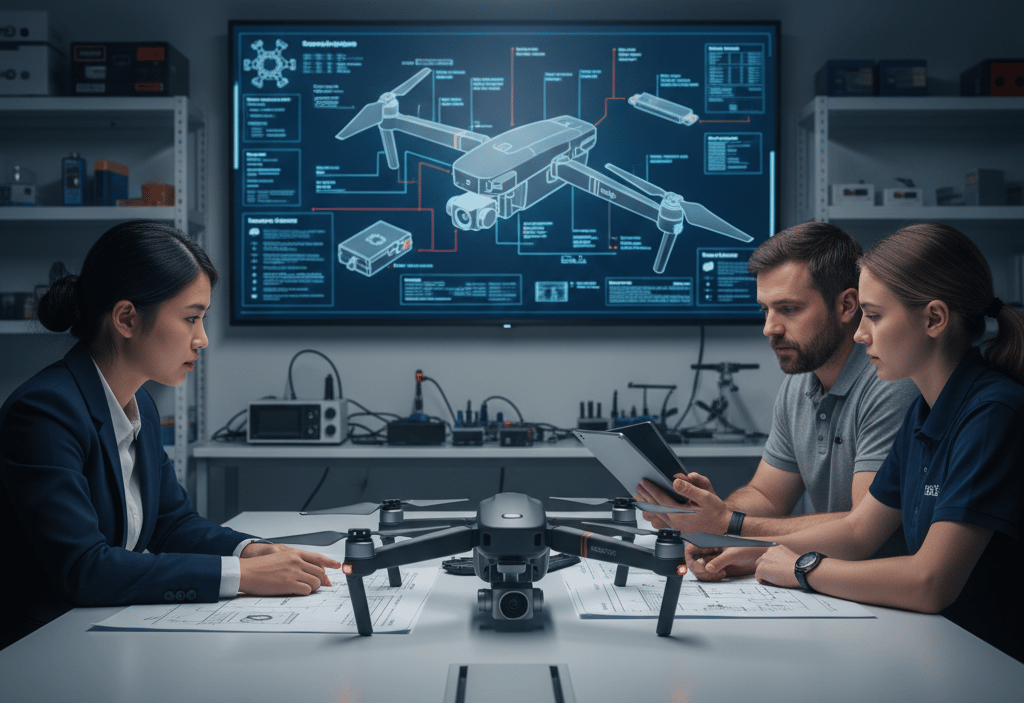
Reverse engineering is typically a multi-stage process that varies depending on the target object. Here, we'll outline a general workflow, illustrating each step with realistic images, following our drone's journey.
Before diving in, it's crucial to define the objectives of the reverse engineering effort and gather as much initial information as possible about the target. This includes understanding its purpose, known functionalities, and any available specifications or documentation. Our team begins by examining the external features and reported capabilities of the newly acquired drone.
Here, the engineering team gathers around a table, with the target drone at its center. They are discussing its known specifications and initial observations, outlining their strategy and areas of focus for the reverse engineering project.
2. Disassembly and External Examination
For physical objects, the first practical step is careful disassembly. This involves opening up the device and visually inspecting its internal components. This initial examination helps identify major modules, connections, and any obvious design choices. Our engineers meticulously begin to take the drone apart.
Here, a lead engineer carefully disassembles the drone, using specialized tools to remove panels and expose internal wiring. They are taking notes and photographing each step to ensure a clear record of the drone's original construction.




3- Component Identification and Analysis
Once disassembled, individual components are identified. This often involves reading part numbers, consulting datasheets, and using specialized equipment to understand their function. For integrated circuits (ICs), this might involve decapping and microscopic analysis.
In this image, a microscope is being used to examine the intricate details of a microchip on a circuit board. This allows for the identification of smaller components and their connections, which are often not visible to the naked eye.


4- Data Extraction and Software Analysis (for Digital Systems)
For software and firmware, this stage involves extracting the code and then using specialized tools like disassemblers and debuggers to understand its logic. This transforms machine code into a more human-readable assembly language, which can then be further analyzed.
Here, a cybersecurity analyst uses a disassembler tool to examine the assembly code of a software program. They are looking for specific functions, data structures, and control flows to understand how the program operates.
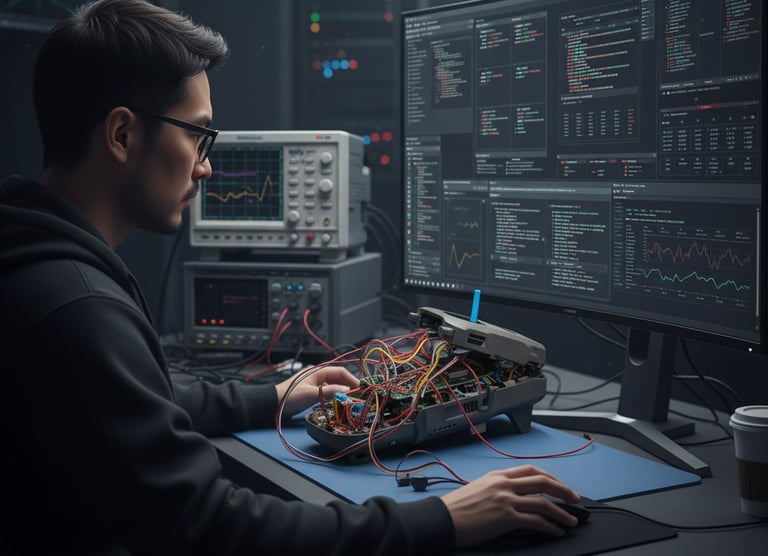

5- Functional Analysis and Prototyping
Once components and code are understood, the next step is to analyze their interactions and overall system functionality. This might involve setting up test benches, simulating parts of the system, or even creating functional prototypes based on the reverse-engineered knowledge.
In this image, engineers are testing a reverse-engineered circuit using an oscilloscope and a power supply. They are measuring voltage levels and signal waveforms to verify their understanding of the circuit's operation under various conditions.


Contact Us Today
Ready to unlock the secrets of complex systems or optimize your own designs? Our team of experienced reverse engineering specialists is here to help. Reach out to us to discuss your project, and let's turn challenges into solutions


